How To Bypass Microsoft Defender Cloud Apps 2025
- Get link
- X
- Other Apps
Bypassing Microsoft Defender Cloud Apps Blocking with SSH Tunneling and FoxyProxy
With Microsoft Defender for Endpoint (E5 license) and Microsoft Defender for Cloud Apps, organizations can block access to unsanctioned web apps using native integration (see official documentation). However, it is possible to bypass this control by tunneling web traffic through an SSH server and using a proxy add-on like FoxyProxy in the browser.
Before Bypass – Blocked by Defender Cloud Apps
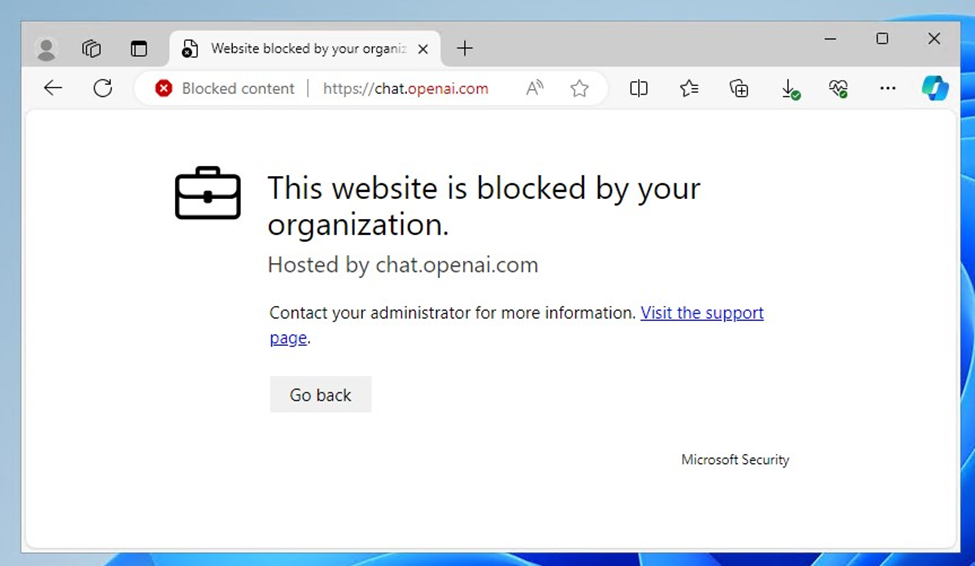
The Bypass Technique: Step-by-Step
- Set up a VPS or VM you control (e.g., on DigitalOcean, AWS, etc.) with SSH access.
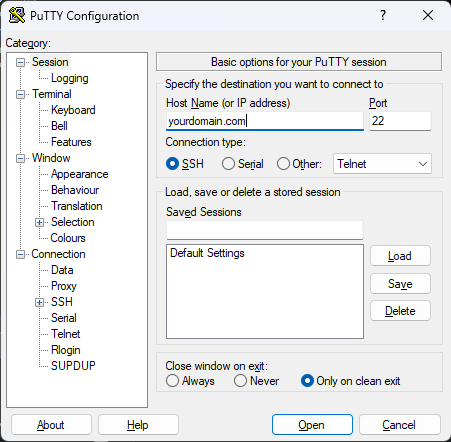
- Start an SSH SOCKS5 Tunnel on your machine with the following command:
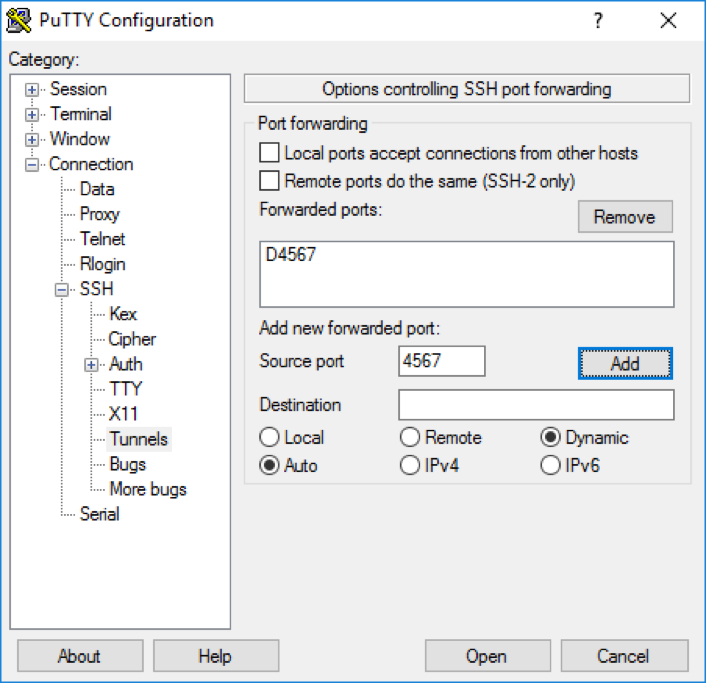
For Windows users, you can use PuTTY to set up a dynamic tunnel underssh -D 8123 -q -C -N username@your-vps-ipSSH > Tunnels. - Install FoxyProxy on your browser (Firefox/Chrome).
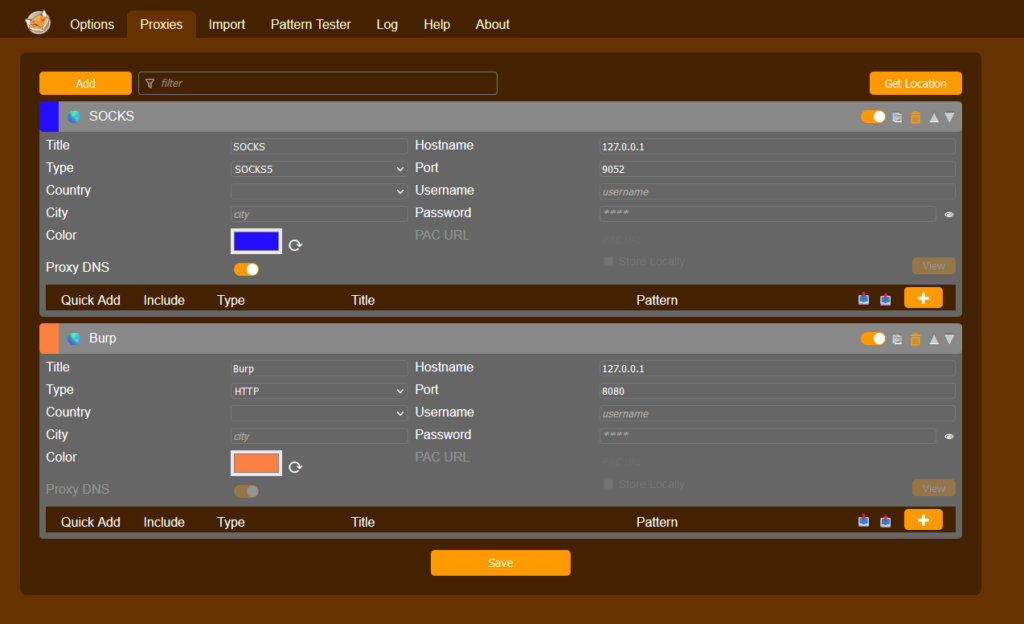
- Configure the proxy:
- Type: SOCKS5
- Hostname: 127.0.0.1
- Port: 8123
- Enable Proxy DNS
- Pattern:
*://*/*(to tunnel all traffic)
- Activate the proxy profile in FoxyProxy.
- Test access to previously blocked sites — they will now be accessible through the SSH tunnel.
After Bypass – Successful Access via SSH Tunnel
Why This Works
Microsoft Defender’s network protection and Cloud App control features work based on traffic visibility. When a user routes all traffic through a SOCKS5 tunnel over SSH, it encrypts and hides the destination traffic from the endpoint’s network visibility. This effectively bypasses controls set by the administrator.
Mitigation Recommendations
- Block outbound SSH (port 22) traffic to untrusted IPs.
- Monitor for usage of SSH clients (PuTTY, MobaXterm, etc.).
- Detect and block browser extensions like FoxyProxy.
- Use Endpoint DLP and App Control to prevent tunneling tools.
Security controls are effective only when users cannot bypass them. Always monitor, restrict, and enforce based on behavior, not just access points.
- Get link
- X
- Other Apps
Comments
Post a Comment